The proliferation of online meetings due to COVID-19 is leading to widespread adoption of virtual event participation across a wide range of business and personal uses, which is the good news.
The not-so-good news is that unscrupulous individuals are also picking up on the growing popularity of virtual meetings, and trying to exploit them. It is important to prevent your private event content — sometimes containing sensitive data and intellectual property — from being shared by attendees, who also need to be free from worry while participating.
As an event organizer, you need to pay close attention to virtual event security issues related to online get-togethers; here are 10 tips to keep your virtual events safe and secure for your users:
1. Market your event directly to your target audience
Exclusivity is a good thing when it comes to virtual events. Instead of plastering your event marketing all over the internet, consider using targeted advertising technology to get your event in front of attendees who are actually interested in the subject matter. Utilize email lists, public relations and advertising in industry trade publications, and direct marketing tactics to reach the people that matter. This way you have less chance of inadvertently attracting predatory entities to your event.
2. Protect your content and hide video/streaming URL
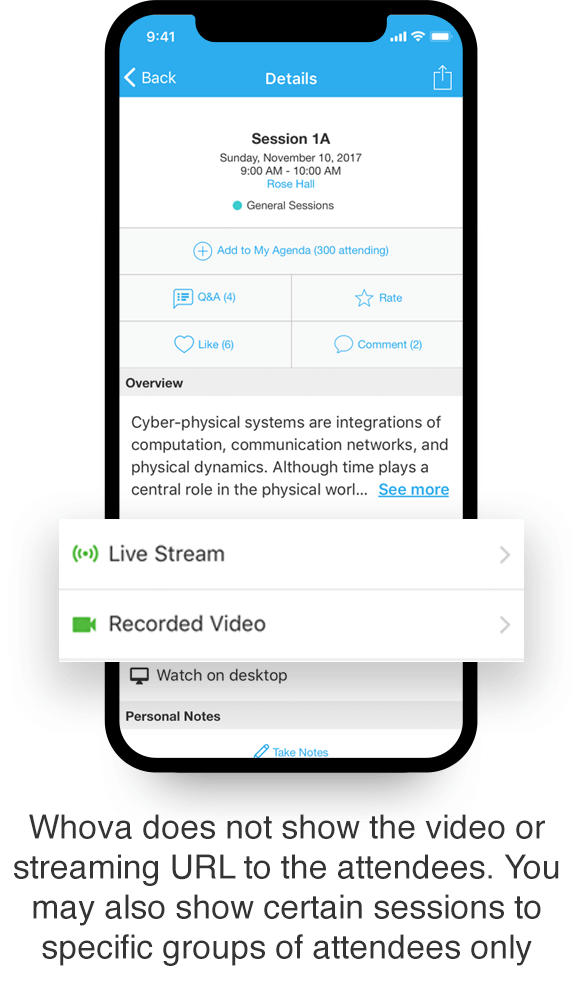
Another major concern for event organizers is how to keep your content from being stolen and passed around the internet without your approval or knowledge. Web conferences are often a wealth of information. You are there to help your attendees learn something about your organization or to share some sensitive information with them. But, there is a risk that someone will get a hold of your content and start sharing it with others.
Virtual event apps like Whova secure your content by preventing the URL of your information from being displayed. It means that anyone who attends your event will not be able to access your content without your knowledge. At the same time, Whova also allows you to show specific sessions only to certain groups of attendees.
3. Use a webinar instead of a meeting
Meetings are great for full collaboration and interaction between all participants, but webinars include several features that will majorly prevent Zoom bombing or any other disruptions during the event. A Zoom webinar will only allow content sharing, audio, and video for panelists, and attendees are automatically in “Listen & View Only” mode when they join a session. This puts who can participate and affect the session into your hands!
4. Promote registration in advance to pre-screen attendees
Getting to know who is attending your event in advance is crucial to blocking nuisance attendees from negatively impacting your event. Build an easy to use, yet secure online registration page, and set a date for registration at least three business days in advance of your event. This has the dual effect of motivating interested parties to sign-up before the registration expires, and allowing you to review attendees. When building your registration forms, require more than just a name and working email address; ask for the individual’s employer, work title, and work email or phone number. This will help you cross-reference any registrations that sound alarm bells.
5. Choose the right platform
Let’s face it – some virtual event meeting software is just better than others. Select one that meets your needs, whether you are hosting a virtual conference, webinar, or hybrid event. Do research before selecting your provider, paying close attention to customer testimonials, reviews, and industry experience. As a general rule of thumb, experienced, well-reviewed providers are usually the ones with the most robust information technology architecture and experienced development teams to provide the most worry-free online meeting experience.
6. Educate attendees about security
Ensure your attendees know best practices before they join your event. Remind them about these security basics:
- Do not accept any unsolicited chat requests from people with suspicious profile during the event
- Don’t give out your email addresses to other attendees you don’t trust
- Refrain from sharing their screens with fellow attendees or anyone during the event
- Check their computer or mobile device for the latest security update before joining the event
7. Monitor your audience and remove unwanted guests and contents
Assign someone on your staff to monitor attendee behavior during your virtual events, looking for complaints from other attendees, foul language, or other disruptive behavior. Keep an eye on anyone who has registered with a generic ID or email address such as @gmail, @yahoo, etc. as these are popular with hackers. If you find that someone is disrupting a meeting, you can kick them out under the “Participants” tab. Kick them out using your virtual meeting platform’s participant settings, and make sure you disable their ability to rejoin. Once the event begins, do not accept any unregistered attendees.
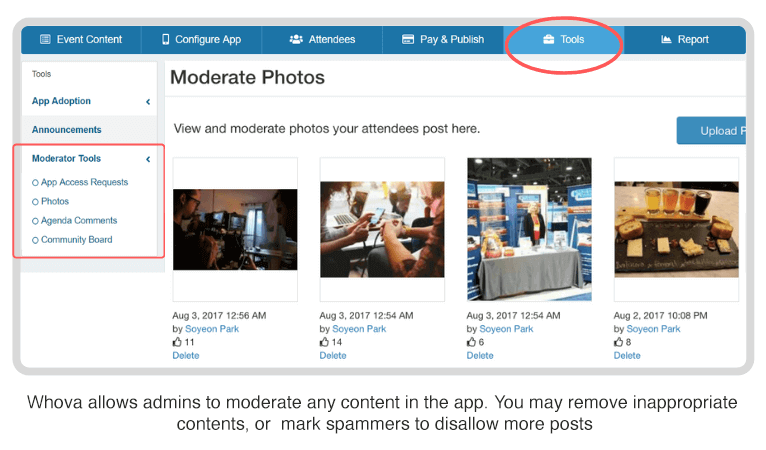
Virtual event platforms such as Whova has many moderations tools to help you monitor the attendance and contents.
8. Password protect meetings
Providing randomly generated passwords with letters, numbers, and unique characters is the most effective way to avoid password guessing by hackers. Access codes are also popular; however, limit their reuse across multiple events to cut-down on the possibility that some may have leaked to the wrong people.
9. Check the streaming settings to make sure you have the most secure options
Take an extra cautionary step by ensuring that you have the safest possible settings enabled. By checking the meeting settings you can choose to not allow attendees to rename themselves or unmute themselves, disallow anonymous questions, disable chats between participants that cannot be moderated, and even prevent non-authenticated users from joining the call at all, making sure that you always know exactly who is in each session. To learn more about Zoom’s recommended settings, you can also read more here.
10. Authenticate attendees
Passwords are great, but you can also use multi-factor authentication (MFA) for added security. Although it sounds fancy, it’s really just a way to say you need to require multiple different credentials from attendees, like a password you sent them along with the email they used to register, and perhaps the name of their employer. Different providers utilize different methods, but at the very least you should have some screening process in place to only allow signed-in users to participate in your virtual event.
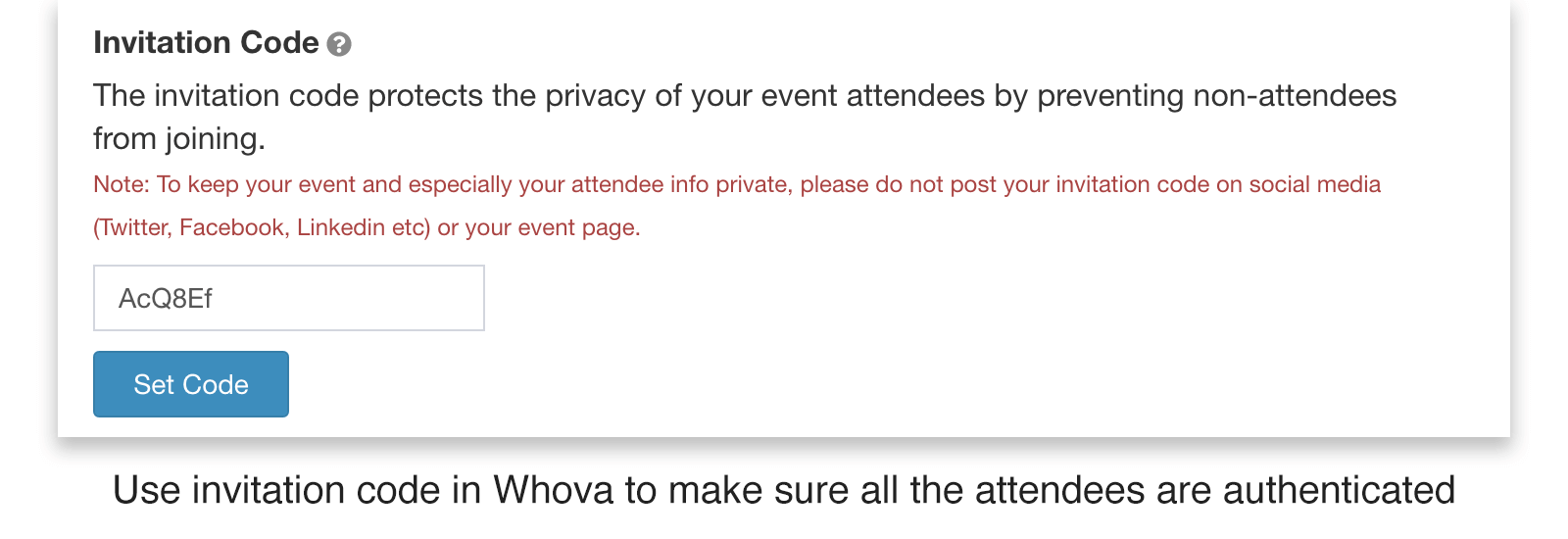
If you are using Whova, you may set up the invitation code so the person whose email is not in your attendee list and does not have the invitation code cannot join the event or view the content at all.
11. Use waiting rooms
A waiting room screens participants before they’re granted access to your event. When attendees join, the host is notified by a tone or name announcement. If such a technology is not available, simply require the meeting hosts to ask new attendees to identify themselves. This gives you an added layer of control over your event security.
12. Turn off screen sharing for your attendees.
Even if you are able to monitor your attendees and keep non-registered attendees out you could still face the problem of inappropriate screen sharing from those at the event. The best way to prevent anyone else from sharing their screens during the meeting is to simply turn off the sharing feature for everyone except yourself and co-host. This will help you avoid any uncomfortable situations if someone decides to share their screen that may have questionable or inappropriate material on it.
Virtual event security is important to keeping your attendees’ information private and your event content safe. For your business or organization, it’s essential to keeping your brand reputation intact. Making an effort ahead of time to plan for a secure event is key to keeping everyone safe and satisfied.
If you are interested to learn more about Whova and how to keep your event secure, you may book a live demo or request a trial account here:
Related Case Studies
